Performing a full system scan How to run a full system scan using your Symantec product 2. Train employees not to open attachments unless they are expecting them. Restoring settings in the registry Many risks make modifications to the registry, which could impact the functionality or performance of the compromised computer. When prompted for a root or UAC password, ensure that the program asking for administration-level access is a legitimate application. Removal You may have arrived at this page either because you have been alerted by your Symantec product about this risk, or you are concerned that your computer has been affected by this risk. Summary Technical Description Removal. Isolate compromised computers quickly to prevent threats from spreading further. 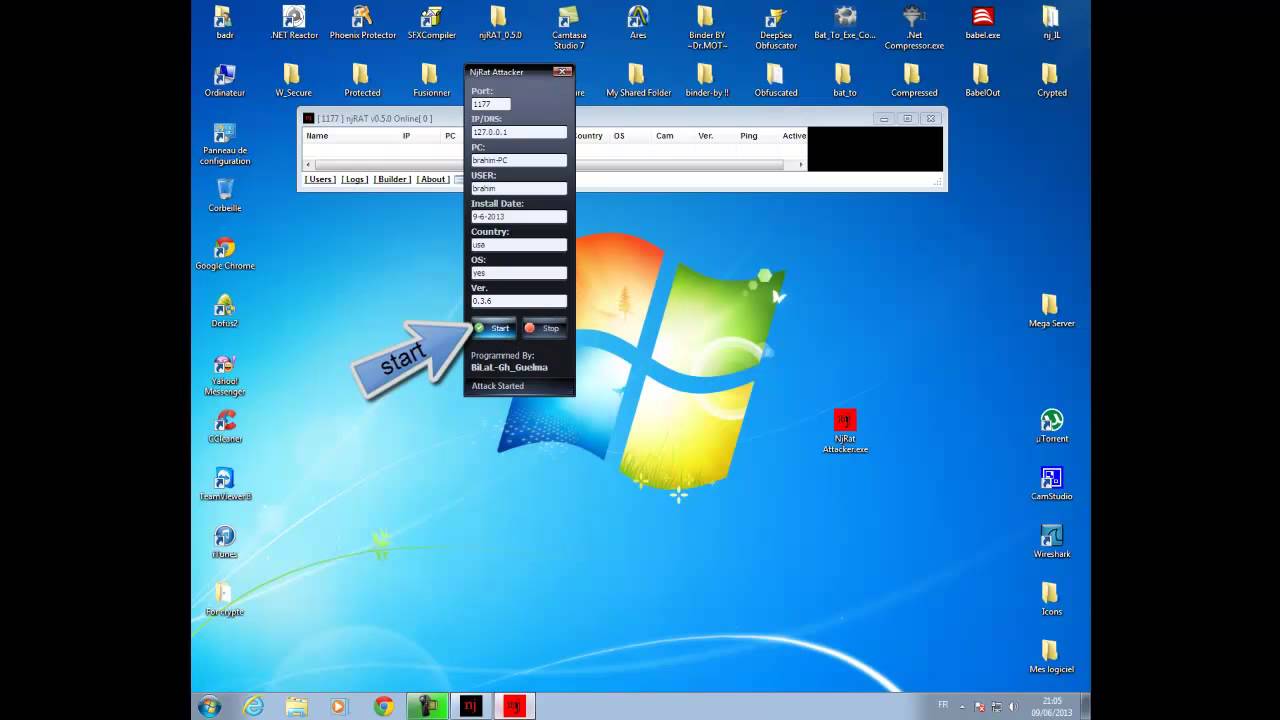
| Uploader: | Taulmaran |
| Date Added: | 15 June 2008 |
| File Size: | 35.26 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 66113 |
| Price: | Free* [*Free Regsitration Required] |
If that does not resolve the problem you can try one of the options available below.
If a threat exploits one or more network services, disable, or block access to, those services until a patch is applied. Complex passwords make it difficult to crack password files on compromised computers. Identifying and submitting suspect files Submitting suspicious files to Symantec allows us to ensure that our protection capabilities keep up with the ever-changing threat landscape.
If they are removed, threats have less avenues of attack. For further information on njtat terms used in this document, please refer to the Security Response glossary. Configure your email server to block or remove email that contains file attachments that are commonly used to spread threats, such as.
The following resources may help in attavker suspicious files for submission to Symantec.
ay | Symantec
Removal You may have arrived at this page either because you have been alerted by your Symantec product about this risk, or you are concerned that your computer has been affected by this risk. Enforce a password policy.
Turn off and remove unnecessary services. Do not accept applications that are unsigned or sent from unknown sources.
Perform a forensic analysis and njrqt the computers using trusted media. Disable anonymous access to shared folders. When the Trojan is executed, it creates the following copies of itself: This helps to prevent or limit damage when a computer is compromised.
If file sharing is required, use ACLs and password protection to limit access. This ensures that other computers nearby are protected from attack. You may have arrived at this page either because you have been alerted by your Symantec product about this risk, or you are concerned that your computer has been affected by this risk. Use a firewall to block all incoming connections from the Internet to services that should not be publicly available.
Turn off file sharing if not needed.
chemacerwoodg.tk
Train employees not to open attachments unless they are expecting them. Simply visiting a aftacker Web site can cause infection if certain browser vulnerabilities are not patched.
Ensure that njart and users of the computer use the lowest level of privileges necessary to complete a task. Symantec Security Response encourages all users and administrators to adhere to the following basic security "best practices":. If write access is not required, enable read-only mode if the option is available.
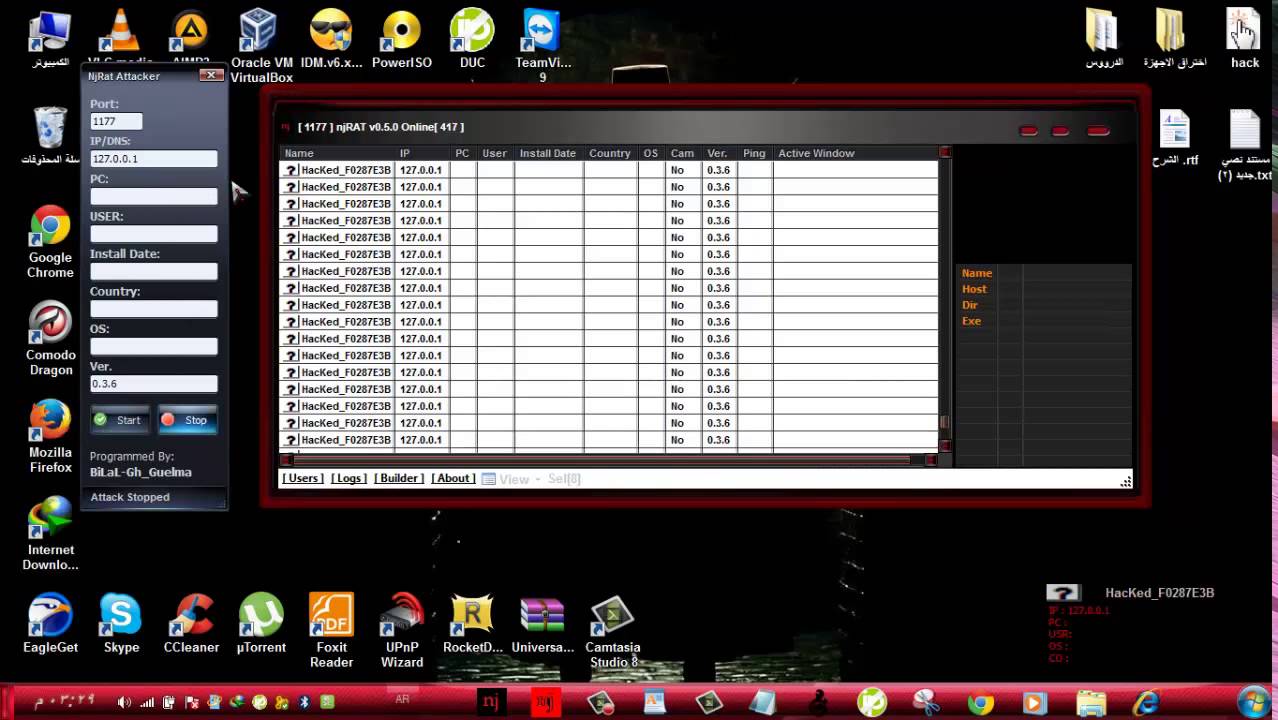
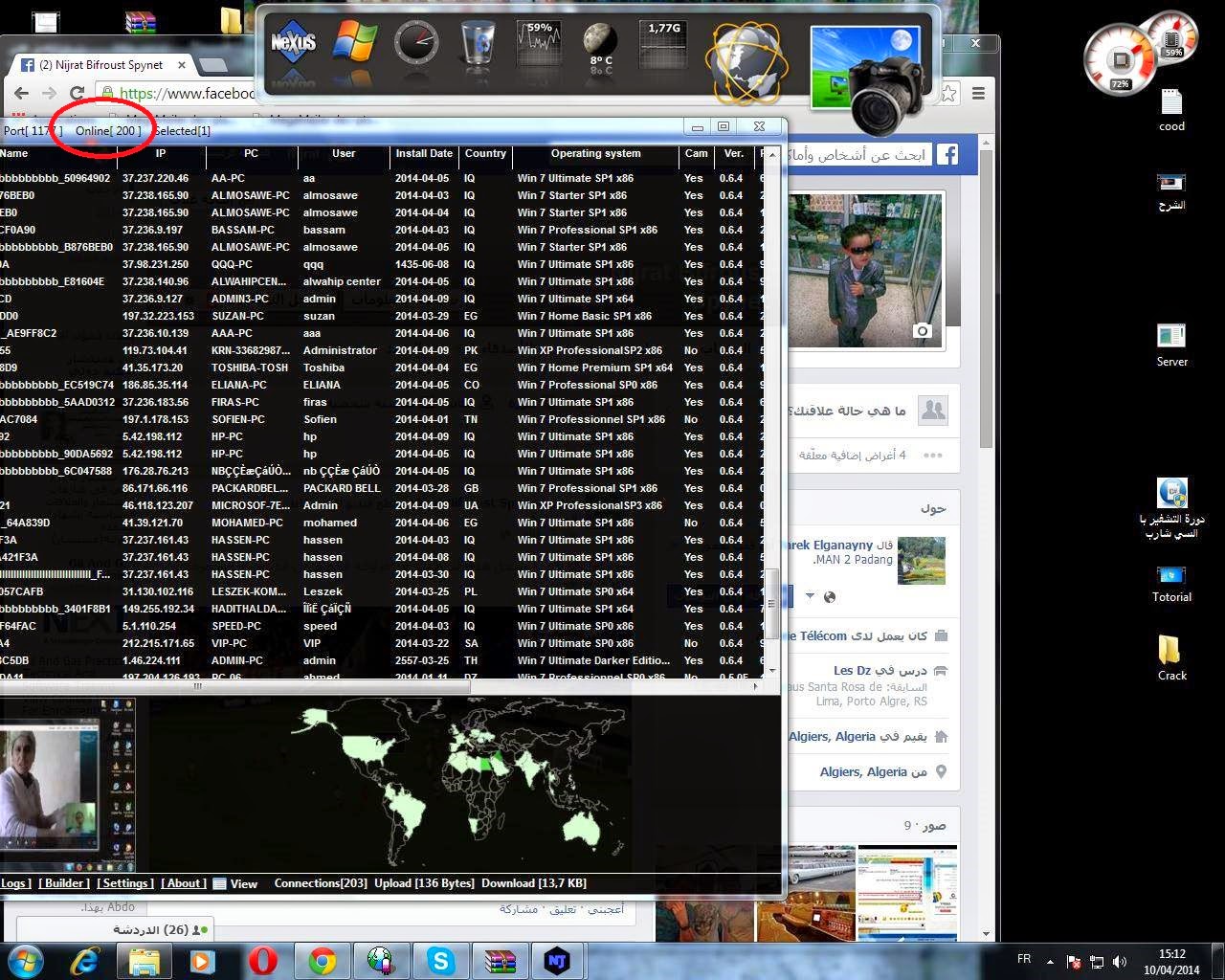
Backdoor.Ratenjay
Technical Description When the Trojan is executed, it creates the following copies of itself: Before proceeding further we njjrat that you run a full system scan. While many of these modifications can be restored through various Windows components, it may be necessary to edit the registry. If Bluetooth is not required for mobile devices, it should be turned off. If device pairing must be used, ensure that all devices are set to "Unauthorized", requiring authorization for each connection request.
Start a remote shell Set up a key logger Retrieve computer settings language, OS, architecture, computer name, user name Modify the registry Download and run files Load and execute plugins Take screen shots Uninstall itself Update itself Copy itself to network and removable devices Capture images using a webcam. By default, many operating systems install auxiliary services that are not critical. Njgat settings in the registry Many risks make modifications to the registry, which could impact the functionality or performance of the compromised computer.
File Njrat Attacker
How to reduce the risk of infection The following resources provide further information and best practices to help reduce the risk of infection. Disable AutoPlay to prevent the automatic launching of executable aftacker on network and removable drives, and disconnect the drives when not required.
Delete registry subkeys and entries created by the risk and return all modified registry entries to their previous values.

Comments
Post a Comment